Digital forensics: หลักสูตร EC-Council Security Specialist (ECSS)
A Complete Guide to Pass EC-Council ECSS Exam.
EC-Council Certified Security Specialist (ECSS) เป็นหลักสูตรที่เน้นการสอนพื้นฐานและแนวทางปฏิบัติที่สำคัญในด้านความปลอดภัยทางไซเบอร์ โดยเนื้อหาของหลักสูตรจะครอบคลุมหัวข้อสำคัญ เช่น:
✅ Information Security – ทำความเข้าใจเกี่ยวกับการจัดการข้อมูลที่ปลอดภัย เทคนิคการป้องกันการรั่วไหลของข้อมูล และแนวทางการเข้ารหัสข้อมูลที่มีประสิทธิภาพ
✅ Network Security – เรียนรู้เกี่ยวกับวิธีการป้องกันเครือข่ายจากการโจมตี การตั้งค่าไฟร์วอลล์ (Firewall) และระบบการป้องกันเครือข่าย (Intrusion Prevention Systems – IPS)
✅ Computer Security – ทำความเข้าใจเกี่ยวกับการจัดการความปลอดภัยของระบบคอมพิวเตอร์ การป้องกันมัลแวร์ และการตอบสนองต่อเหตุการณ์ด้านความปลอดภัย
เตรียมสอบหลักสูตรด้านความมั่นคงปลอดภัยระดับพื้นฐาน
ผู้เชี่ยวชาญด้านความปลอดภัยที่ผ่านการรับรองจากสถาบัน EC-Council Certified Security Specialist (ECSS) ช่วยให้นักเรียนได้พัฒนาทักษะของตนเองในสามด้านที่แตกต่างกัน ได้แก่ ความปลอดภัยของข้อมูล ความปลอดภัยของเครือข่าย และนิติคอมพิวเตอร์
ความปลอดภัยของข้อมูลมีบทบาทสำคัญในองค์กรส่วนใหญ่ ความปลอดภัยของข้อมูล การประมวลผลข้อมูล และการสื่อสารได้รับการคุ้มครองจากการรักษาความลับ ความสมบูรณ์ และความพร้อมของข้อมูลและการประมวลผลข้อมูล ในการสื่อสาร ความปลอดภัยของข้อมูลยังครอบคลุมถึงการรับรองความถูกต้องของข้อความที่น่าเชื่อถือ ซึ่งครอบคลุมการระบุถึงการตรวจสอบและการบันทึกการอนุมัติและการอนุญาตข้อมูล การไม่เปลี่ยนแปลงข้อมูล และการไม่ปฏิเสธการสื่อสารหรือข้อมูลที่จัดเก็บ
Why is ECSS Important?
Upon Completion of this Course, you will accomplish following:-
- Key issues plaguing the information security, network security, and computer forensics
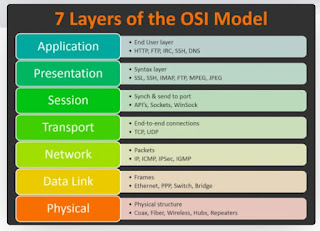
- Fundamentals of networks and various components of the OSI and TCP/IP model
- Various types of information security threats and attacks, and their countermeasures
- Identification, authentication, and authorization concepts
- Different types of cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools
- Fundamentals of IDS and IDS evasion techniques
- Data backup techniques and VPN security
- Fundamentals of firewall, techniques for bypassing firewall, and firewall technologies
- such as Bastion Host, DMZ, Proxy Servers, Network Address Translation, Virtual Private
- Network, and Honeypot
- Social engineering techniques, identify theft, and social engineering countermeasures
- Different stages of hacking cycle
- Various network security protocols
- Wireless Encryption, wireless threats, wireless hacking tools, and Wi-Fi security
- Different types of web server and web application attacks, and countermeasures
- Fundamentals of ethical hacking and pen testing
- Incident handling and response process
- Cyber-crime and computer forensics investigation methodology
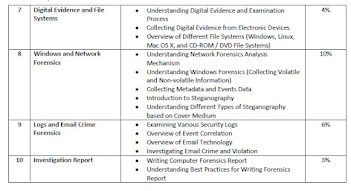
- Different types of digital evidence and digital evidence examination process
- Different type of file systems and their comparison (based on limit and features)
- Steganography and its techniques
- Different types of log capturing, time synchronization, and log capturing tools
- E-mails tracking and e-mail crimes investigation
- Writing investigation report
- Gathering volatile and non-volatile information from Windows and network
- forensics analysis mechanism
- Computer Forensics Fundamentals : หลักการพื้นฐานด้านนิติคอมพิวเตอร์
- Digital Evidence: หลักฐานดิจิทัล
- Windows Forensics: นิติวิทยาระบบปฎิบัติการวินโดว์
- Network Forensics and Investigating Network Traffic : นิติวิทยาระบบเครือข่าย
- Email Crime and Computer Forensics : อาชญากรรมทางจดหมายอิเล็กทรอนิกส์และนิติคอมพิวเตอร์
- Writing Investigation Report : การจัดทำรายงานการตรวจพิสูจน์หลักฐาน
ประกาศนียบัตรสากล EC-Council Security Specialist (ECSS) Exam Information
Exam Details:Number of Questions: 50
Passing Score: 70%
Test Duration: 2 Hours
ใครที่เหมาะสมกับการเรียน ECSS?
หลักสูตร ECSS ออกแบบมาให้เหมาะกับบุคคลหลากหลายกลุ่ม ไม่ว่าจะเป็น:
✔️ นักเรียนและนักศึกษา ที่ต้องการเริ่มต้นในสายงานความปลอดภัยไซเบอร์
✔️ เจ้าหน้าที่ IT และ Network Administrator ที่ต้องการเพิ่มทักษะด้านความปลอดภัยเครือข่าย
✔️ ผู้ที่สนใจในด้าน Cybersecurity และต้องการสร้างพื้นฐานที่แข็งแกร่งในด้านนี้
✔️ บุคลากรด้าน IT ที่ต้องการเตรียมความพร้อมในการป้องกันภัยคุกคามทางไซเบอร์ในองค์กร
Test Format: Multiple Choice
By getting familiar with the environment and ECSS exam questions repeatedly, you will strengthen your confidence and thus lessen anxiety, thus enhance time management skills, and also identify your weak areas and work upon them. By answering ECSS practice questions, you also acquire skills to deal with different question types and find tactics that work best for you to pass the EC-Council ECSS exam.
ตัวอย่างแบบทดสอบ (EC-Council ECSS Questions )
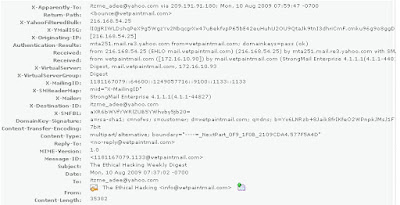
hashes for a set of characters?
project. Now, you want to know the IP address of the sender so that you can analyze various
information such as the actual location, domain information, operating system being used, contact
information, etc. of the email sender with the help of various tools and resources. You also want to
check whether this email is fake or real. You know that analysis of email headers is a good starting
point in such cases. The email header of the suspicious email is given below:
Compensation Office with the following message:
If Maria replies to this mail, which of the following attacks may she become vulnerable to?
Dear Sir/Madam,
My name is Edgar Rena, the director of compensation here at the MN Compensation Office in
Chicago. We receive so many complaints about fraudulent activities that have been taking place in
your region for the past few years. Due to the high volume loss of money, the MN compensation
department has had an agreement with the appropriate authority to compensate each victim with a
sum of USD$500,000.00.
You were selected among the list of people to be paid this sum. To avoid any imperative mood by
intending scammers, your payment has been transmuted into an International bank draft which
can be cashed at any local bank in your country.
Please fill the below details and send it to our secretary for your compensation bank draft.
Full name: ______
Address: ________
Tel: ____________
Fill & Send to:
Dr. Michael Brown
MN Compensation Office, IL
Tel: +1-866-233-8434
Email: micbrown@live.com
Further instructions shall be given to you by our secretary as soon as you contact him. To avoid
losing your compensation, you are requested to pay the sum of $350 for Insurance Premium to
our secretary.
Thanks and God bless.
Rate now:
victim?
- หลักสูตร CYBER FORENSICS ASSOCIATE (CFA)
- หลักสูตร Computer Hacking Forensic Investigator (C|HFI)
- หลักสูตร Digital Forensics Essentials (DFE)
- eCDFP exam Review
EC-Council Certified Security Specialist (ECSS คือ)
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง Admin เพื่อแก้ไขต่อไป
ขอบคุณครับ
#WindowsForensic #ComputerForensics #dfir #forensics #digitalforensics #computerforensic #investigation #cybercrime #fraud
.png)



%20map.png)






No comments:
Post a Comment