Mobile Forensics:How to Extract Evidence From Samsung Galaxy A13
Forensic Imaging & DATA Extraction
Evidence Intake Phase
|
Brand |
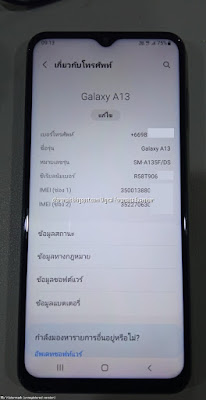
Samsung |
|
Device Name/ Model number |
Samsung Galaxy / SM-A135F |
|
Android Version |
Android 12 |
|
Baseband version |
SP1A.210812.016.A135FXXU2AV |
|
Kernel Version |
4.19198 |
|
Build Number |
SP1A.210812.016.A135FXXU2AVJ3 |
|
Serial Number |
- |
|
MicroSD Card |
64 |
Preparation Phase
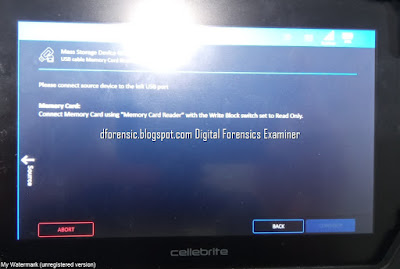
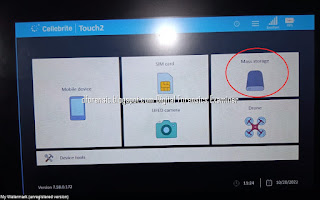
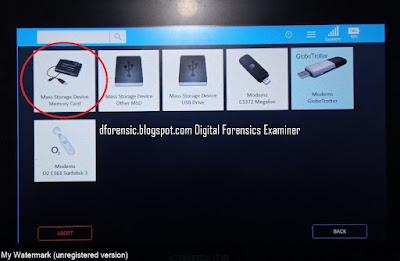
How to Prepare an Android Device for Acquisition
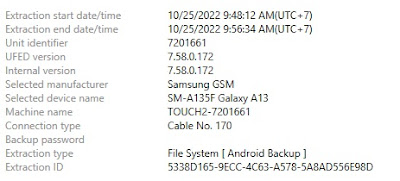
- Cellebrite Physical Analyzer 7.30.0.228
- Cellebrite UFED 7.58.0172
- Samsung Galaxy A13
- USB Cable 170
- Lenovo Workstation
Isolation Phase
Before the examination, Android devices should be isolated from networks that can be connected with Android devices via wireless (Wi-Fi), infrared and Bluetooth network capabilities. Isolation of the mobile from these communication sources is a significant phase before examination because it prevents the adding of new data to the phone during new calls and texting. Remote wiping or remote access
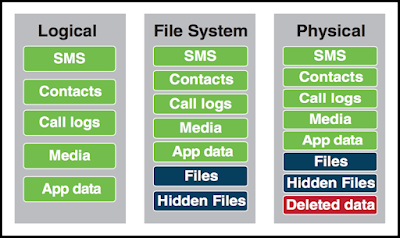
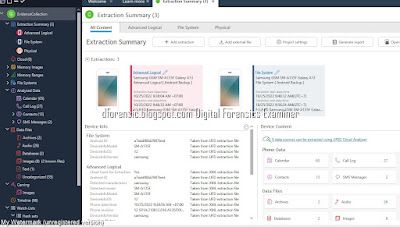
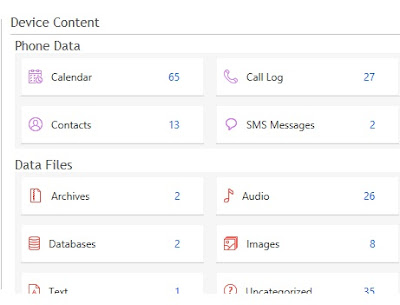
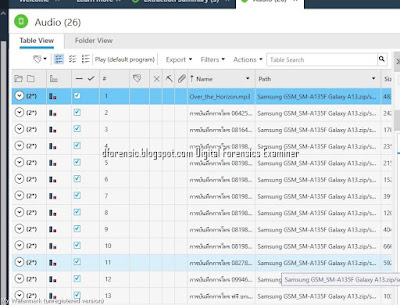
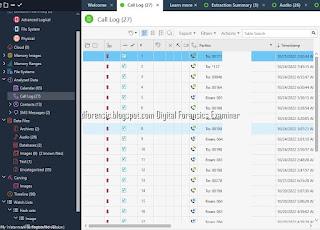
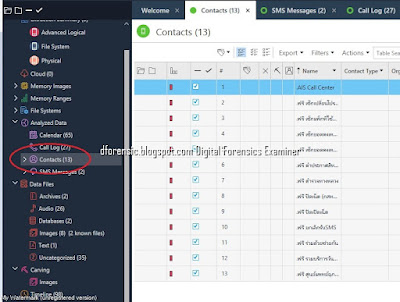
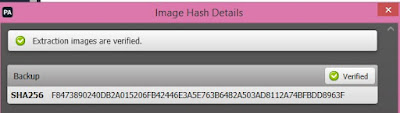
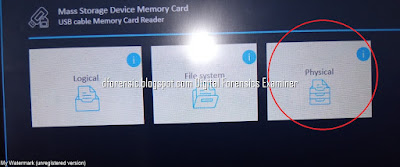
Summary of types of data that can be extracted using logical, file system and physical extraction. Source: Cellebrite article
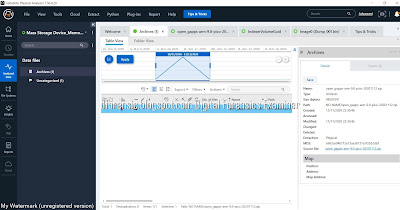
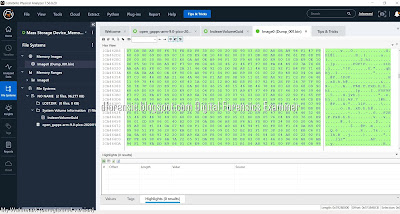
UFED Physical Analyzer Examination
ขั้นตอนการตรวจสอบพิสูจน์พยานหลักฐานทางดิจิทัล ( DIGITAL FORENSICS )เป็นอย่างไร
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง Admin เพื่อแก้ไขต่อไป
ขอบคุณครับ
#WindowsForensic #computerforensic #ComputerForensics #dfir #forensics #digitalforensics #investigation #cybercrime #fraud