Digital Forensics: TryHackMe Forensics writeup.
This challenge is based on Memory Forensics
This is a memory dump of compromised system, do some forensics kung-fu to explore the inside.
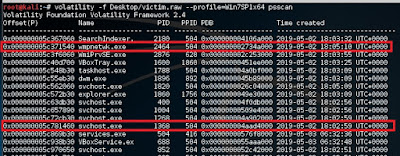
Looking for ‘SearchIndexer’ PID
#volatility -f Desktop/victim.raw --profile=Win7SP1x64 pslist | grep SearchIndexer
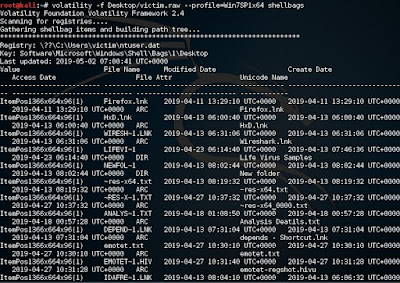
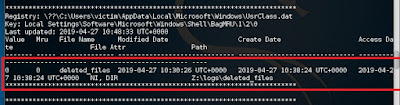
This information is stored by Windows using two registry keys called ShellBags.
#volatility -f victim.raw --profile=Win7SP1x64 shellbags
Last accessed directory
The ‘deleted_file’ is the last directory accessed by the user.
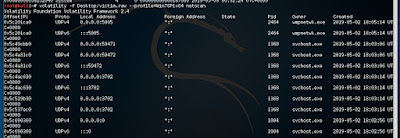
Let ‘s scan the open port using the following command
First we need to find a suspicious open port. Use netscan to find out open ports:
#volatility -f Desktop/victim.raw --profile=Win7SP1x64 netscan
PID 1368,2464 with multiple ports which look suspicious
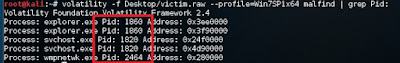
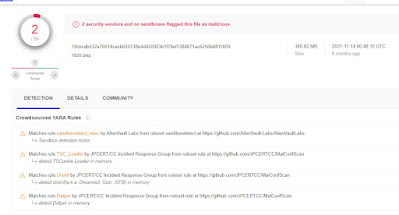
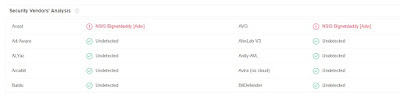
How about dump the process and check with Virus total?
1820.dmp 1820 shows malicious sign. 2 security vendors and no sandboxes flagged this file as malicious
We can dump the memory using the following command.
#volatility -f victim.raw -p <malicious PID> --profile=Win7SP1x64 memdump <Directory to save the file>
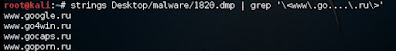
# strings Desktop/malware/1820.dmp | grep '\<www\.ic......\.com\>'
# strings Desktop/malware/1820.dmp | grep '\<202\....\.233\....\>'
# strings Desktop/malware/1820.dmp | grep '\<209\.190\....\....\>'
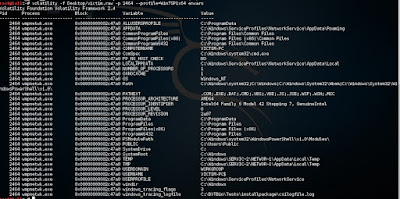
To check with the environment variable from the memory image
#volatility Desktop/victim.raw -p 2464 --profile=Win7SP1x64 envars
อ่านเพิ่ม Memory Forensics
หมายเหตุ:เนื้อหาในเว็บไซต์นี้มีขึ้นเพื่อวัตถุประสงค์ในการให้ข้อมูลและเพื่อการศึกษาเท่านั้น
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง Admin เพื่อแก้ไขต่อไป
ขอบคุณครับ
#WindowsForensic #computerforensic #ComputerForensics #dfir #forensics
#digitalforensics #investigation #cybercrime #fraud






No comments:
Post a Comment