DIGITAL FORENSICS: Booting a forensics image on a Virtual Machine
When performing forensic investigation on an image of a target system drive, it is often necessary to recreate and examine the live environment of the system to acquire all relevant data during the investigation. By running the image as a live system, the investigator can perform a live forensic analysis of the image, allowing for the potential discovery of additional forensic artifacts that may not have been previously uncovered from a traditional static analysis. Finally, because the system is running in a protected virtual environment created from the forensic image file, there is no risk of compromising the target system.
To access this feature from the Start screen, simply click the Boot Virtual Machine icon or module button as shown above.
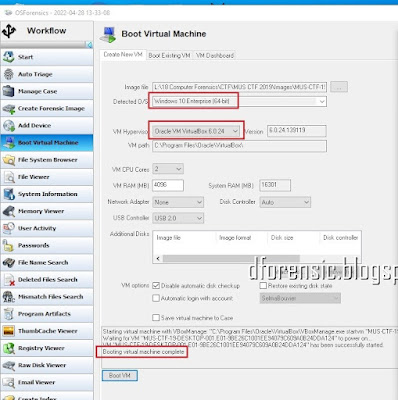
Users simply need to point OSF to the forensic image file of the target O/S drive, review a few other options and features and click the ‘Boot VM’ button.
Steps
- 1. Select image file.
- 2. Choose OS if image is of a multi-boot system.
- 3. Choose VirtualBox or VM Workstation. (Must be pre-installed)
- 4. Review technical specifications.
- 5. Attach any additional disk images.
- 6. Choose or review VM options and User account to boot.
- 7. Click “Boot VM”
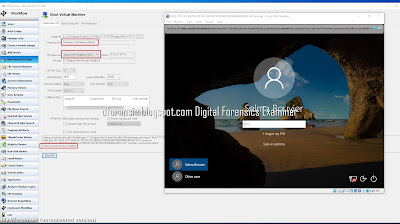
Analyzing the Live System
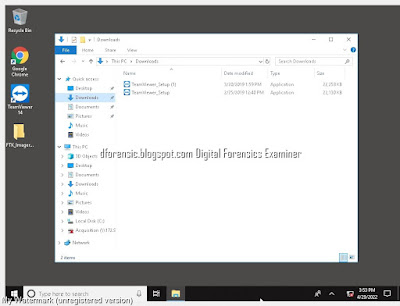
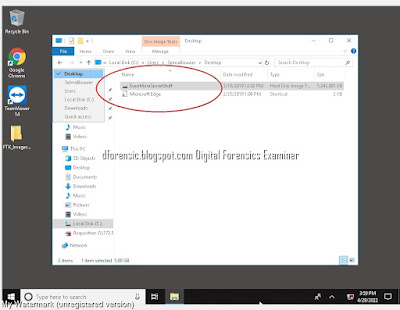
Once the boot process is complete, you may begin analyzing and searching through the live system. In addition to being able to review the Desktop layout, the Recycle Bin, and proprietary files in their native application, this also provides a great visual aid for screenshotting evidence to present to a client or in court when necessary.
Screenshots allow you to capture evidence files and artifacts just as they may have appeared through the eyes of the user. Some examples include…
- Jumplists (recent webpages, Word docs, etc.)
- Autorun Apps.
- Previous custom desktop backgrounds
- Settings for certain applications (e.g., CCleaner)
- Search term history from P2P and other applications
Booting a forensic image in VirtualBox with FTK Imager
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง Admin เพื่อแก้ไขต่อไป
ขอบคุณครับ
#WindowsForensic #computerforensic #ComputerForensics #dfir #forensics
#digitalforensics #investigation #cybercrime #fraud








No comments:
Post a Comment