Digital Forensics:CAPTURE THE FLAG:DRUG DEALER CASE
วันนี้มาแนะนำการแข่งขัน Belkasoft CTF ซึ่งจัดโดยบริษัท Belkasoft เป็นโซลูชันด้านนิติวิทยาศาสตร์และ incident response ที่ใช้งานง่ายและมีประสิทธิภาพซึ่งช่วยลดความซับซ้อนและเร่งขั้นตอนการสืบสวนทางดิจิทัล โดยกิจกรรมจะเปิดและปิดเป็นช่วง May 2021
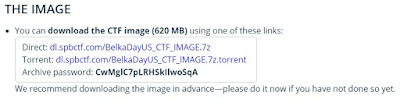
Direct: dl.spbctf.com/BelkaDayUS_CTF_IMAGE.7z
Torrent: dl.spbctf.com/BelkaDayUS_CTF_IMAGE.7z.torrent
Archive password: CwMglC7pLRHSkIlwoSqA
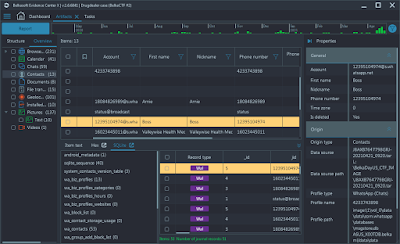
Phone Image
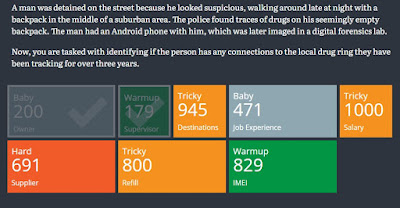
The background of a case?
1. What is the full name of the phone owner?
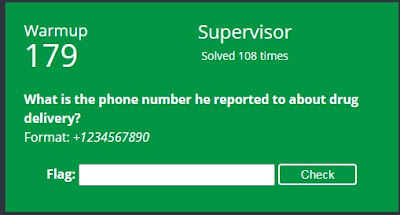
2.What is the phone number he reported to about drug delivery?
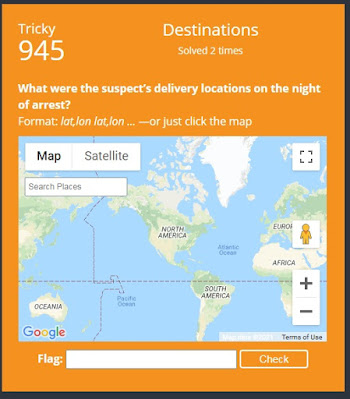
3.What were the suspect’s delivery locations on the night of arrest?
Flag
Camelback Golf Club, 7847 N Mockingbird Ln, Scottsdale, AZ (33.5542226,-111.9340928)
2013 W Harwell Rd., Phoenix, AZ (33.374304,-112.1035501)
33°29'04.2"N 111°52'38.0"W (33.4845,-111.877215)
4.How long has the suspect been acting as a drug dealer?
- So now we see an interview on June 20th, 2020 and an arrest date of April 18th, 2021. If we navigate to https://www.timeanddate.com/date/duration.html and enter those dates (To include the date of the arrest) we get the flag
Solution without Belkasoft X
- The logic is the same
Flag
303 days
5.From what Bitcoin wallet did he get paid the last time for his job ?
Flag
113JqY3CqsQPT7EN6wj5tRAVKftEP9rQC
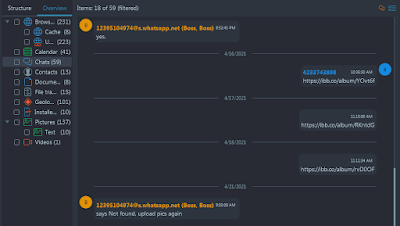
6.What is the phone number of the drug supplier?
Solution
- After locating the Signal backup (manually) and the password (any SQLite viewer, this time you do not need WAL or freelist support), you can use an open source tool https://github.com/pajowu/signal-backup-decode as follows:
/root/.cargo/bin/signal-backup-decode --password '04049 19810 47697 72485 91554 88046' signal-2020-12-20-21-04-59.backup - The tool creates an SQLite database with the extracted data. In the 'recipient' table we see two phone numbers: +13148346839 corresponding to profile name horatio0.42k (it's Derek Hor), and +14233767293 which is our target supplier
Flag
+14233767293
7.When was the last time the suspect met his supplier?
Solution
- The same logic and any SQLite viewer will help you to solve the task. This time, SQLite viewer does not necessarily has to support forensic features, so 'DB Browser for SQLite' will do
- For time conversion, use any online converter or the DCode tool
Flag
Sat, 10 Apr 2021 07:30:00 UTC
- For this task, we were given an 'NSA' tool that allows us to look up cellphone registration history. When we look at the tool, we see we need a latitude, longitude, and a date in (MST). Now we must enter the data. Take the data extracted from the Calendar automatically by Belkasoft X or manually by yourself
- Feed every line into the lookup tool. You will get the output of the number of devices found with their IMEIs. Copy the list of IMEIs into an Excel spreadsheet. You can intersect all the lists by duplicates search (meaning that an IMEI was found in more than one location). Just two IMEIs will be common for all the locations, they are 350236009513272 and 332182208414842. One of those is Derek, the other is the supplier
Belkasoft CTF Certificate Participation
BelkaCTF #2 (Drugdealer case)
Refer: https://belkasoft.com/ctf
หมายเหตุ:เนื้อหาในเว็บไซต์นี้มีขึ้นเพื่อวัตถุประสงค์ในการให้ข้อมูลและเพื่อการศึกษาเท่านั้น
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง Admin เพื่อแก้ไขต่อไป
ขอบคุณครับ
#WindowsForensic #ComputerForensics #dfir #forensics #digitalforensics #computerforensic #investigation #cybercrime #fraud #CTF





































No comments:
Post a Comment