Digital Forensics:UAL Log
What Is User Access Logging?
UAL is a feature included by default in Server editions of Microsoft Windows, starting with Server 2012. As defined by Microsoft, UAL is a feature that “logs unique client access requests, in the form of IP addresses and user names, of installed products and roles on the local server.”(Patrick Bennettuser, access-logging-ual-overview ,June 8, 2021)
- User Access Logging (UAL) is enabled by default on Windows Server operating systems, starting with 2012 and later
- Collects user access and system-related statistical data in near real-time
- Examples of services and roles from which data is collected include DNS, DHCP, IIS, WSUS, etc.
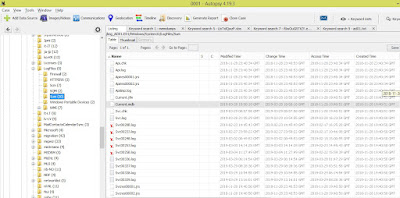
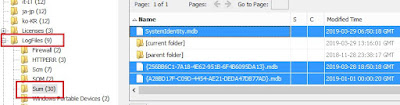
- Stored within multiple .mdb files (ESE databases) located in %SYSTEMROOT%\System32\ LogFiles\SUM
Export UAL log with Autopspy
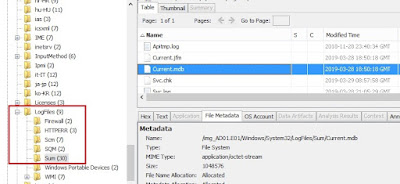
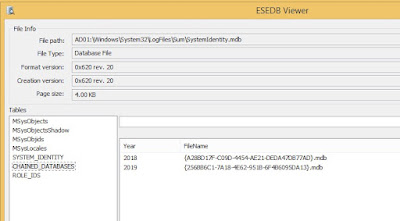
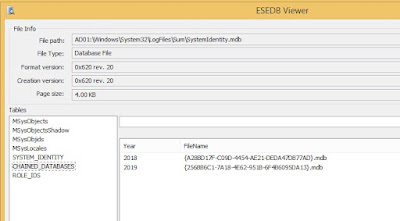
- SystemIdentity.mdb, Current.mdb, and one or more files with a GUID-based name should exist in this location
{GUID}.mdb : Archived data from the Current.mdb, and previous years
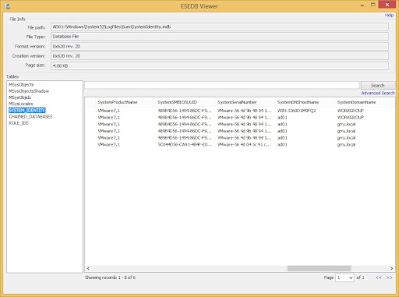
SystemIdentity.mdb : Contains role information and system details
Open with Autopspy
- The GUID-based file names will hold data from the current year, the previous year, and two (2) years prior
Open with ESEDB Viewer
Open with ESEDB Viewer
- Every 24 hours, data from Current.mdb will be copied to the GUID-named database for the current year
- SystemIdentity.mdb will track the other UAL databases and contain basic server configuration info
- This artifact is only present on Windows Server operating systems, 2012 and later
- The IP address tracked is the location from which the associated activity originated; the destination is the Windows Server system from which UAL was obtained
- On the first day of the year, UAL will create a new GUIDnamed .mdb file
- The old GUID-named file is retained as an archive; after two (2) years, the original GUID.mdb will be overwritten
- The activity is tracked by server role, which maps to the roles configured on the Windows Server from which the data was acquired
- This artifact can be used to identify abnormal access to systems and to profile lateral movement from various clients to servers running Windows Server 2012 or later
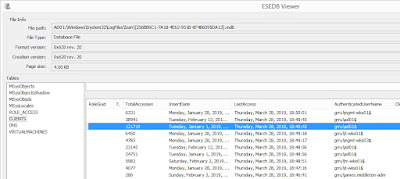
- The InsertDate is logged in UTC, and represents the first access for the year for a combination of the specific user, source IP address, and role
- The LastAccess is logged in UTC, and represents the last access for the year for a combination of the specific user, source IP address, and role
- The “File Server” role is usually associated with SMB access, but in some cases, access via other protocols may be associated with this role
Photo Credit: Microsoft Incident Responders Team
Reference :
- Guidance for Incident Responders ,Microsoft Incident Responders Team
- User Access Logging and KStrike ,Kevin Stokes
- Manage User Access Logging
- Patrick Bennettuser, access-logging-ual-overview :crowdstrike ,June 8, 2021
หมายเหตุ:เนื้อหาในเว็บไซต์นี้มีขึ้นเพื่อวัตถุประสงค์ในการให้ข้อมูลและเพื่อการศึกษาเท่านั้น ช่วยเตือนความจำ
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง Admin เพื่อแก้ไขต่อไป
ขอบคุณครับ






No comments:
Post a Comment