Digital Forensics for Cyber Professionals
By Chad Russell
August 2017
Key Features
- Learn about basic and advanced techniques you will need to gain a grasp on GIAC and other Computer Forensic certifications.
What You Will Learn
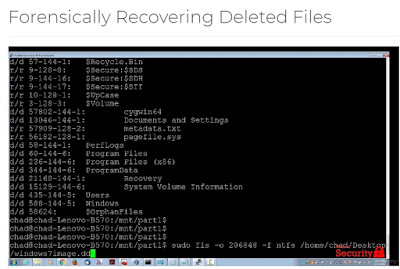
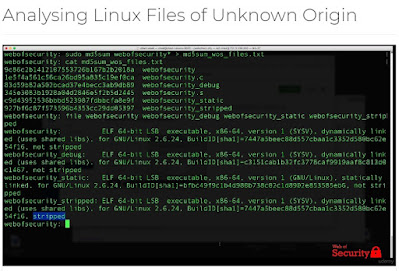
- Learn how to use open source tools to collect digital forensic information from Linux and Windows systems. This course focuses on screencast demonstrations of how to use these tools in a step-by-step manner so you can start doing forensics work immediately on your own.
About
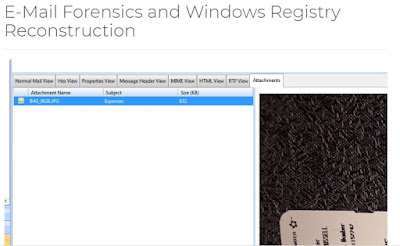
In this course you will learn how to use open source tools to collect digital forensic information from Linux and Windows systems. You will learn how to conduct static malware analysis of live 'Ransomware' using forensics tools and techniques.This course focuses on screencast demonstrations of how to use these tools in a step-by-step manner so you can start doing forensics work immediately on your own. Digital Forensics OverviewRecovery and ReconstructionReversing and Malware AnalysisWindows and Linux Live ResponseIncident Response TechniquesRed and Blue Team Tools Conduct Forensic Analysis of Hacker ActivitiesCAINEForensics Tools and StorageLearn to use open source tools such as CAINE to do forensic analysis on live systems. The Cyber Forensics field is red hot. Stake your claim now!
Style and Approach
This course focuses on screencast demonstrations of how to use these tools in a step-by-step manner so you can start doing forensics work immediately on your own.
Chad Russell
He has been in the CyberSecurity industry for over 15 years. He taught Microsoft Engineering courses as a certified trainer, he managed teams of security engineers and analysts for an internet banking provider, he has been an information security consultant working for companies including SAP, Microsoft and Oracle. He lead and conduct 'Security Risk Assessments' for customers throughout North America with an emphasis on cloud security, identity governance, network security, social engineering, mobile security, breach assessments, database security and access management. Over the past 15 years he held numerous certifications including CISSP, CCNP, MCSE and MCDBA certifications and have a B.S. in Computer Science from Excelsior College. He can help you get certified and get ahead!
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง Admin เพื่อแก้ไขต่อไป
ขอบคุณครับ












No comments:
Post a Comment