Digital Forensics:Browser forensics
Browsers keep a record of visited websites, which can reveal a user's search history and potential malicious activity.
Kroll Artifact Parser And Extractor (KAPE)
KAPE gives you access to targets and modules for the most common operations required in forensic exams, helping investigators gather a wider range of artifacts
Description. ChromeHistoryView is a small utility that reads the history data file of Google Chrome Web browser, and displays the list of all visited Web pages
Google Chrome’s browsing data is stored in the user’s AppData\\Local\\Google\\Chrome\\User Data\\Default directory.
Browser forensics Lab
Instruction
We found an attacker who compromised the machine and download malware . Please help find the URL which use by attacker.
Hint
Reveal download activity from Browser History.
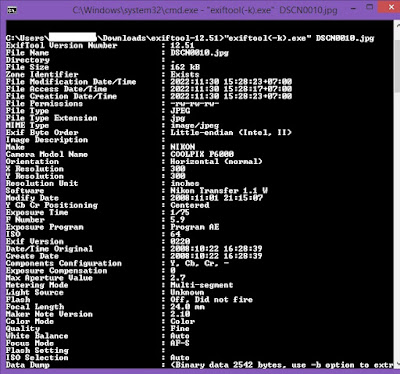
Step 1. KAPE Collecting Browser Artifacts
Step 2. Chrome History provides analysts with the following information:
Chrome History View is a free utility developed by NirSoft
To run it, navigate to where you downloaded and extracted the tool Chrome History View.exe and double click the file.
Step 3. SQLite Viewer Web App
SQLite Viewer Web is a free, web-based SQLite Explorer, inspired by DB Browser for SQLite and Airtable.
Open SQLite Browser and navigate to the Chrome database stored at C\Users\<User Name>\AppData\Local\Google\Chrome\User Data\Default.
Q2.How many times a site was visited (most frequency information) and what the page title by User visits ?
Hint
Reveal download activity from Browser History.
อ่านเพิ่มเติม: How to analyze WebCacheV01.dat



.png)