Windows Forensic:Registry Recon
Features
To solve the Windows Forensics challenges, we used the following resources:
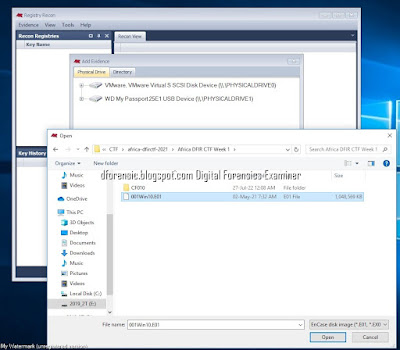
.Registry Recon supports adding forensic images in EnCase (E01) and raw (dd) formats, VHD disk images, physically mounted slave drives, and the contents of directories as evidence.
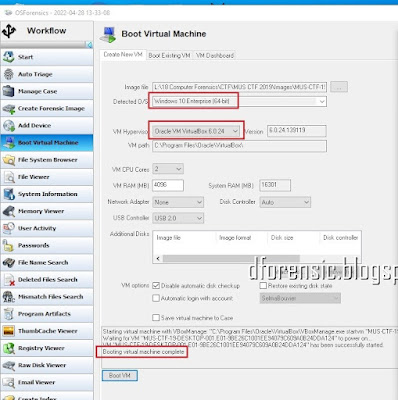
1.Add Evidence
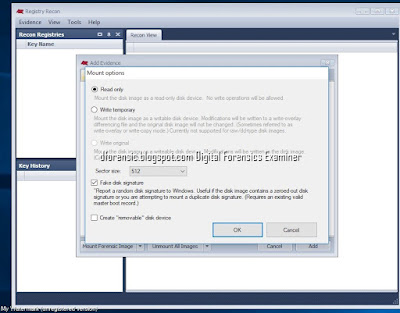
2. Add Evidence >Mount option
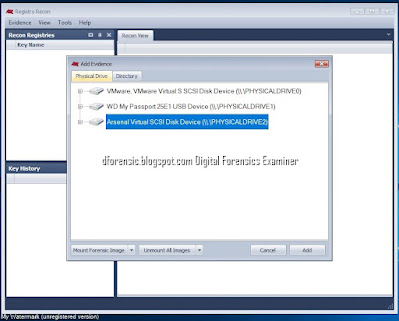
3. Adding Evidence >add
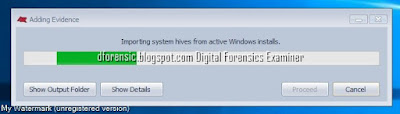
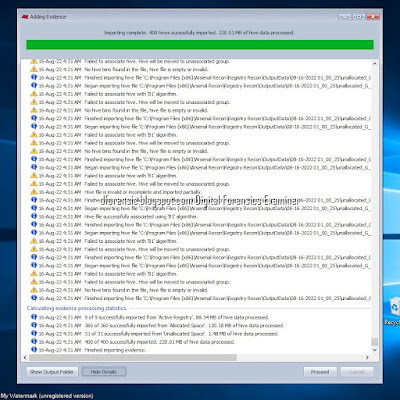
5. Adding Evidence > Importing system hives from active windows installs.
6.Adding Evidence >Importing complete.
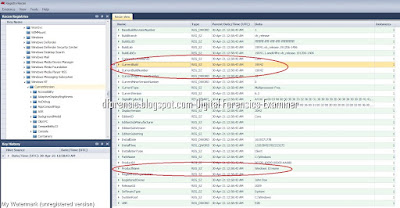
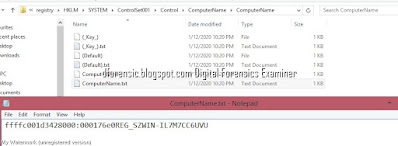
7. #Windows-1 Hostname? (DESKTOP-0J3S8C2)
Open the file using a Registry Recon
SYSTEM\ControlSet001\Control\ComputerName\ComputerName registry key. Note the data value of the ComputerName.
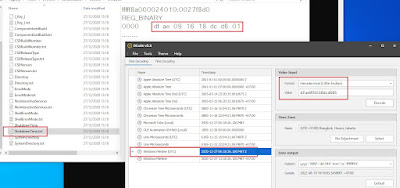
8.# Windows-2 Time-zone (UTC)
Still using the Registry Recon and the SYSTEM file, navigate to the SYSTEM\ControlSet001\Control\TimeZoneInformation registry key. Note the data value for TimeZoneKeyName.
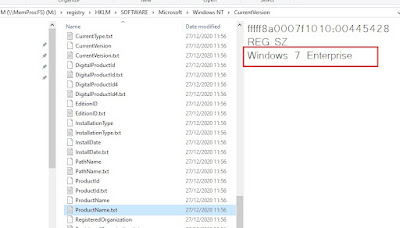
9.#Windows-3 Build number (19042)
Open the Registry Recon then navigate to the Software\Microsoft\Windows Nt\CurrentVersion registry key. Note the data value for the CurrentBuildNumber.
10.#Windows-4 Product name
From the same steps and results obtained from the previous challenge, the product name is also listed there (on the same registry key).
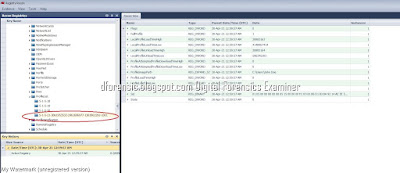
11. #Windows-5 SID (John Doe)
You can also determine a user's SID by looking through the ProfileImagePath values in each S-1-5-21 prefixed SID listed under:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
Select each SID under this in turn and look at the ProfileImagePath and at the end of this string is the name of the user.
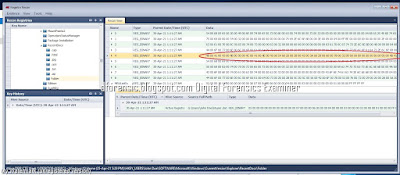
12. Windows-6 TypedURLs (http://go.microsoft.com)
The last link entered is a bit different. In our case, the browser used is Internet Explorer and the urls are also in the hive. Other browsers usually keep their data in other locations on the drive. The path to the key is NTUSER.DAT\SOFTWARE\Microsoft\Internet Explorer\TypedURLs and the value we are looking for is the first value named url1. The answer is (http://go.microsoft.com)
13.Windows-7 Recently accessced docs folder (HACKPLANET)
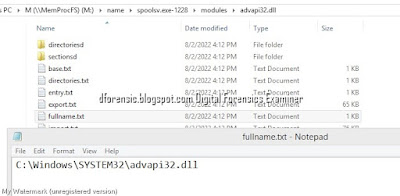
14.Windows-8 Run (OneDrive.exe)
The key takeaway from the description is “Finding a software that runs when system is restarted”.
So we go to the software registry in Windows\system32\config\ and under Microsoft\Windows\Current Version\Run\, in the execute key
ปัญหาที่พบ
- โปรแกรมยังไม่สามารถ Automate decode ได้ เราต้อง copy ค่าใน Registry ไป Decode โดยเครื่องมืออื่น ๆ
- supports forensic images (E01) and raw (dd) formats, VHD disk images, physically mounted slave drives, and the contents of directories as evidence แต่ไม่สนับสนุน *.L01,*.AD
Introducing Registry Recon
Refer:Registry Recon
How to Find a User's Security Identifier (SID) in Windows
#WINDOWSFORENSIC #COMPUTERFORENSICS #DFIR #FORENSICS #DIGITALFORENSICS #COMPUTERFORENSIC #INVESTIGATION #CYBERCRIME #FRAUD #หลักสูตรการพิสูจน์หลักฐานทางดิจิทัล
หมายเหตุ:เนื้อหาในเว็บไซต์นี้มีขึ้นเพื่อวัตถุประสงค์ในการให้ข้อมูลและเพื่อการศึกษาเท่านั้น
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง ADMIN เพื่อแก้ไขต่อไป
ขอบคุณครับ
หมายเหตุ:เนื้อหาในเว็บไซต์นี้มีขึ้นเพื่อวัตถุประสงค์ในการให้ข้อมูลและเพื่อการศึกษาเท่านั้น
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง ADMIN เพื่อแก้ไขต่อไป
ขอบคุณครับ