Mobile Forensics: free mobile training course
หลักสูตรอบรมการตรวจพิสูจน์อุปกรณ์สื่อสารเคลื่อนที่
Belkasoft offers a free self-paced course Mobile Forensics with Belkasoft X.
We know how expensive your time is and how difficult it is to plan things now. This is why we prepared a course you get to study in a safe, comfortable environment and at times that are convenient for you. This course can be accessed online anytime until March 31, 2022.
To participate in the training, please do the following:1) If you do not have a Belkasoft Evidence Center X license yet, request a trial at https://belkasoft.com/trialPut “Mobile Self-Paced Course” in the Comment field2) Download and install Belkasoft Evidence Center X3) Complete the training using the form at https://belkasoft.com/
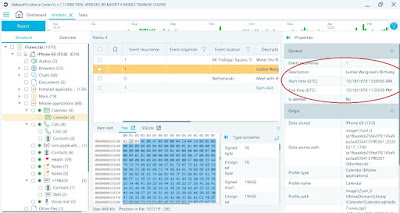
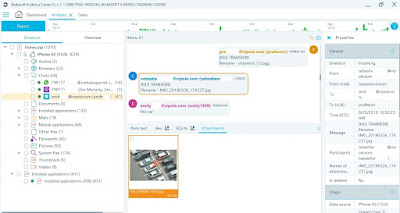
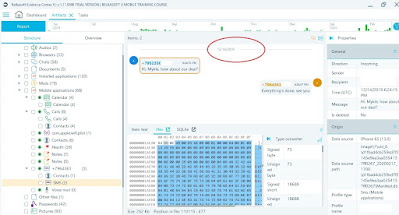
Watch a short tutorial video on how to work with found artifacts
Webinar on locked iPhones acquisition
ที่มา: belkasoft.com
* หากมีข้อมูลข้อผิดพลาดประการใด ขออภัยมา ณ ที่นี้ด้วย รบกวนแจ้ง Admin เพื่อแก้ไขต่อไป
ขอบคุณครับ
#WindowsForensic #ComputerForensics #dfir #forensics #digitalforensics #computerforensic #investigation #cybercrime #fraud